Csrss.exe is C:/Windows/System32/ located file on Windows Operating System. It is Microsoft safe process that helps to manage graphical instruction sets in a majority in windows OS. The file description of CSRSS properties on Microsoft Windows is “Client Runtime Server Process.” Csrss.exe is executable in Windows and used as a standard system process. Some malware regularly utilizes a procedure name of “Csrss.exe” to camouflage itself. Any record named “Csrss.exe” in another catalog might be viewed as malware.
Well, csrss.exe primarily works to store your personal information related to your cards, social security number, ID, email addresses, websites that you surfed or surfing habits, IP addresses, etc. But if this csrss.exe Trojan gets in wrong hands, then it could affect your life as they are using your all details to steal your money or use your identity for criminal purpose.
If you remove csrss.exe, it will start killing the process and you will notice the Blue screen will appear on a windows screen. This happens because people are misconfused about Csrss.exe that is malware and should be removed as soon as possible otherwise it will damage to the window system. There is much falsehood hoax deliberately antivirus software that claims that it is a malware which is not malware.
If Csrss.exe Virus infects your Laptop/PC, then it may contact to remote host are as follows:
To report to its author a fresh infection and for setup or other information to be received. Arbitrary files that include updates or extra malware can be downloaded and executed. To be instructed by a distant attacker. To upload information from the computer that has been impacted.
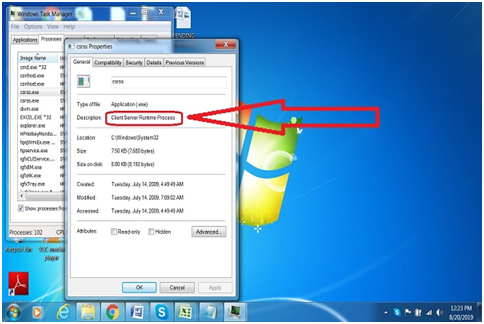
How To Know That Laptop/PC is infected
The simple way to see, if malware is running under the name of “Csrss.exe” infects your Laptop/PC.
The guide underneath is intended to be utilized on the off chance that you speculate that malware is tainted with your Laptop/PC. Because of the number of steps and incalculable projects being used, this malware expulsion manual may appear to be overpowering.
Step # 1. Click CTRL + ALT + DEL on your keyboard to open your Windows Task Manager.
Step # 2. Right-click the Csrss.exe you believe to be malware, and then press “Open place of file.”
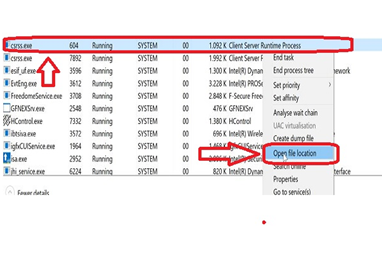
Step #3. The Windows Csrss.exe should be in section C:\Windows\System32. Any file named “Csrss.exe” in another directory may be regarded as malware.
Step #4. You can download RKill by clicking the link below.
By clicking the link below, you can download RKill. This link opens a new internet page to download “RKill.”
Step #5. To prevent malicious programs from running, double click on Rkill program.
Step #6. RKill is going to begin operating in the background now, kindly be patient as this tool looks for malicious method and seeks to stop it.
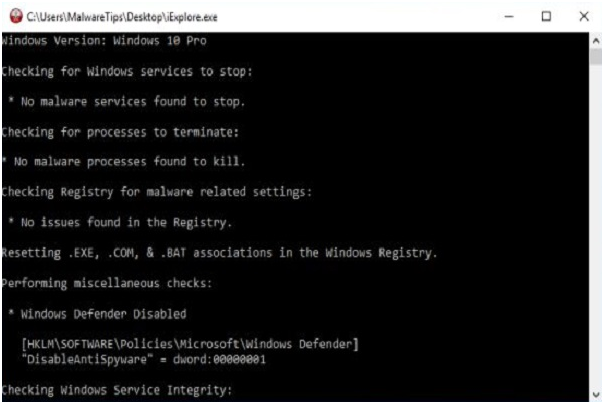
Step #7. Upon completion of the assignment, the Rkill tool will produce a log. After running RKill, do not reboot your computer as malware programs start again.
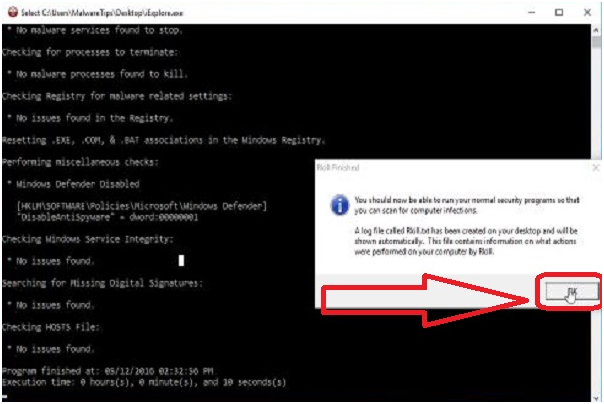
Now use malware bytes to remove malware from Csrss.exe:
Step #8. By clicking the link below, you can download Malwarebytes.
Step #9. Double-click the mb3-setup-consumer-x.x.x.xxxx.exe folder to install Malwarebytes on your PC after Malwarebytes has completed downloading. Downloaded files are saved in the Downloads folder in most cases.
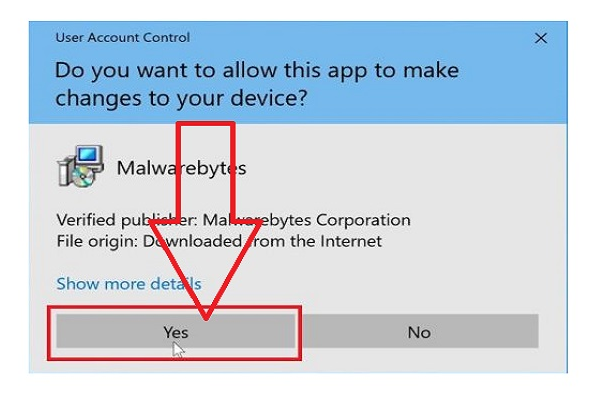
Step #10. You may be asked if you want to allow Malwarebytes to make adjustments to your computer with a User Account Control pop-up. If this occurs, to proceed with the setup, you should press “Yes.”
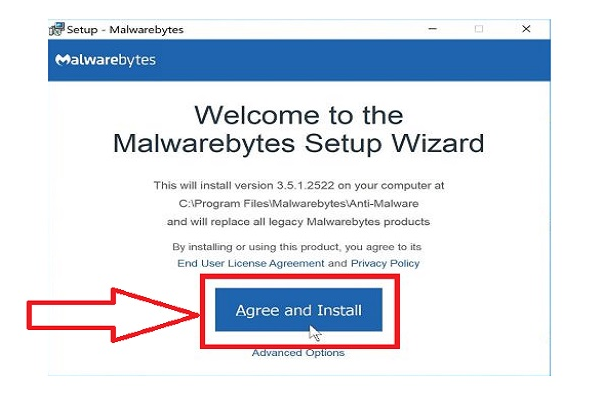
Step #11. Now the setup of Malwarebytes starts, you will see the Malwarebytes Setup Wizard that will guide you through the setup phase. Click the “Agree and Install” button to install Malwarebytes on your PC.
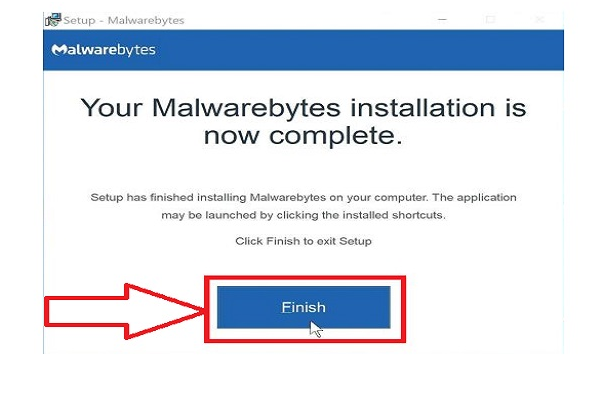
Step #12. Malwarebytes will begin and update the antivirus database automatically once installed. Now you need to click on the “Scan Now” button to perform a system scan.
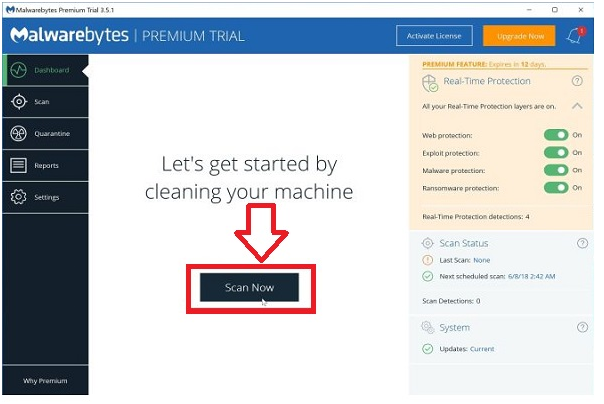
Step #13. Now begin screening adware and other malware programs on your desktop. This method may take a couple of minutes, so we recommend you do something else and check the scan status periodically to see when it is complete.
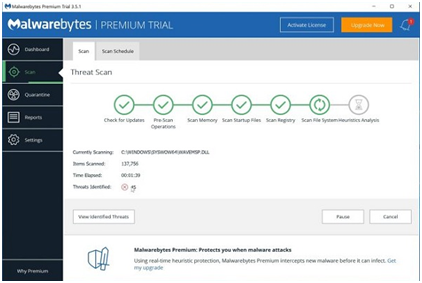
Step #14. Upon completion of the scan, you will receive a screen displaying the malware infections identified by Malwarebytes. Click the “Quarantine Selected” button to remove the malicious programs that Malwarebytes has discovered.
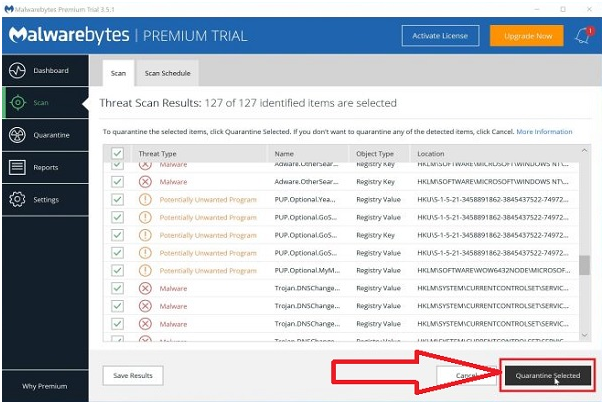
Step #15. Now Malwarebytes remove all of its found malicious documents and registry keys. Malwarebytes may ask you to restart your computer to complete the malware removal process.
Step #16. Malwarebytes can be closed, and the rest of the instructions can continue after the removal process completed.
HitmanPro scanning for the virus Csrss.exe:
Step #17. HitmanPro (https:/malwaretips.com/download-hitman-pro) can be downloaded by pressing the connection below.
Step #18. To install this program on your PC, double-click “hitmanpro.exe” (for Windows 32-bit variants) or “hitmanpro x64.exe” (for Windows 64-bit variants). Downloaded files are saved in the Downloads folder in most cases.
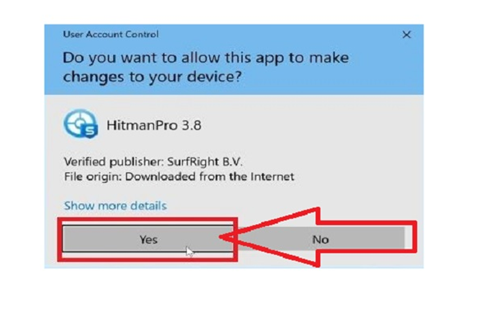
Step #19. You may be asked if you want to allow HitmanPro to create adjustments to your computer with a User Account Control pop-up. If this occurs, to proceed with the setup, you should press “Yes.”
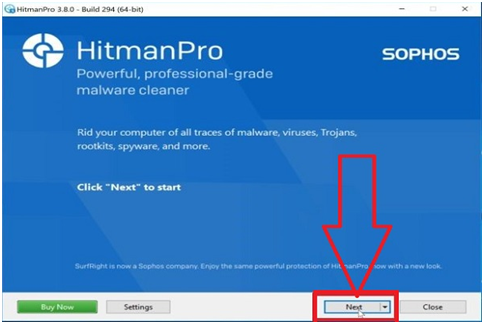
Step #20. You will be shown with the start screen when HitmanPro begins, as shown below. To scan a system, click on the “Next” button.
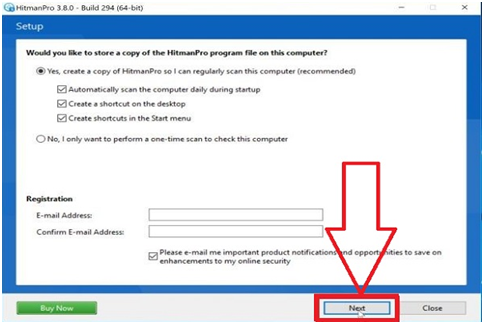
Step #21. Now start scanning for malicious programs on your desktop by HitmanPro. It will take a few minutes to complete this process.
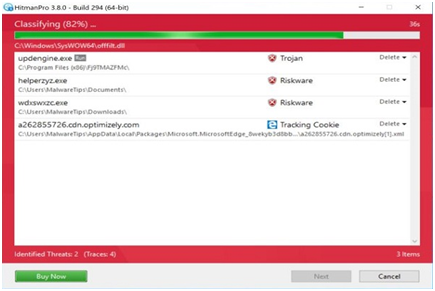
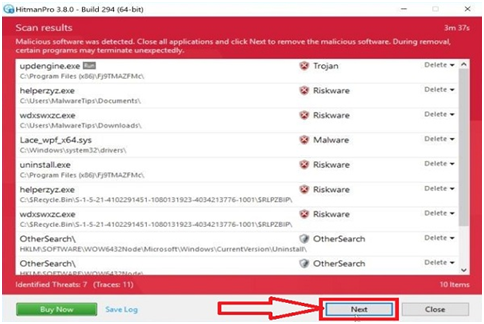
Step #22. Upon completion of the scan, HitmanPro will show a list of all the malware discovered by the program. To remove malicious programs, click the “Next” button.
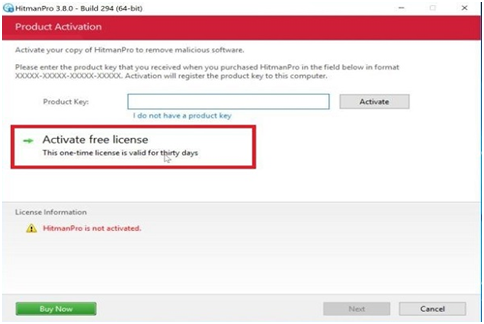
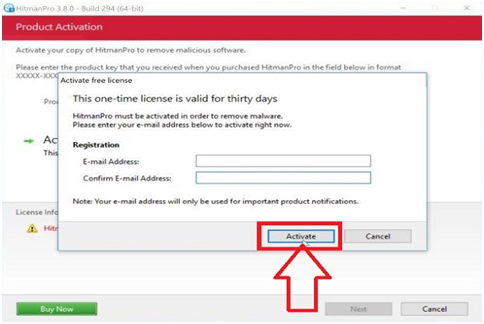
Step #23. To start the free 30-day trial and remove all the malicious documents from your PC, click the “Activate free permit” button.
Step #24. You can close HitmanPro once the process is complete and continue with the rest of the instructions.
To remove potentially unwanted programs, Zemana AntiMalware is free:
Step #25. Zemana AntiMalware (https:/malwaretips.com/download-zemana-antimalware) can be downloaded free of charge by clicking the link below.
Step #26. To begin Zemana AntiMalware setup, double-click the file called “Zemana AntiMalware setup.exe.” In downloads folder, there is a downloaded file from that you can operate.
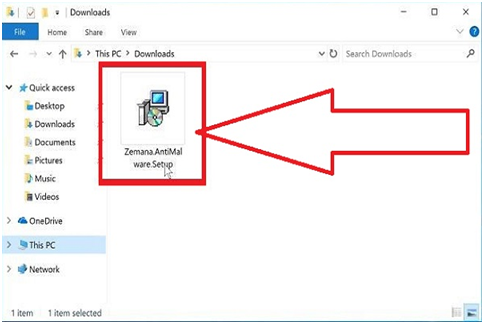
Step #27. To operate this file, you need the “user account control dialog.” If this occurs, to proceed with the setup, you should press “Yes.”
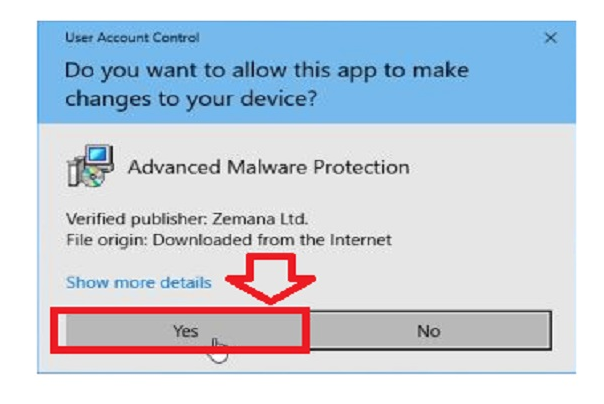
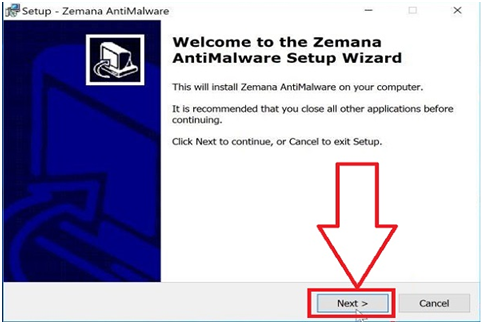
Step #28. To install Zemana AntiMalware on your PC, click the “Next” button. To finish the installation process, follow the on-screen prompts.
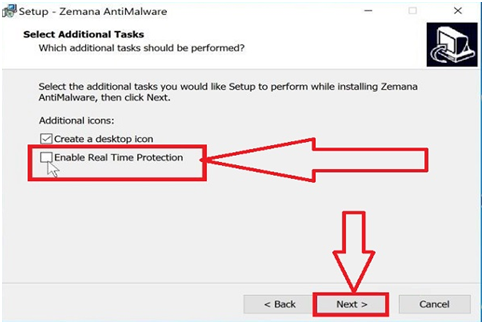
Step #29. You must opt-out of the “Enable Real-Time Protection” option when you reach the “Select Additional Tasks” screen, then press the “Next” button.
Step #30. Click on the “Scan” button to execute a system scan when Zemana AntiMalware starts.
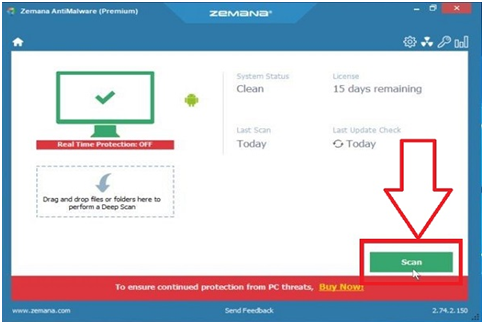
Step #31. Zemana AntiMalware is now scanning for malicious documents on your PC. It may take a few minutes for this phase.
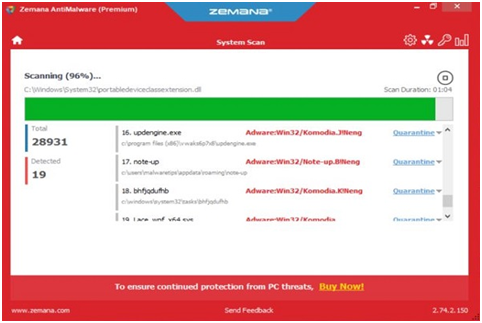
Step #32. Upon completion of Zemana AntiMalware, a list of all the malware discovered by the program will be displayed. To extract malicious documents from your computer, click the “Next” button.
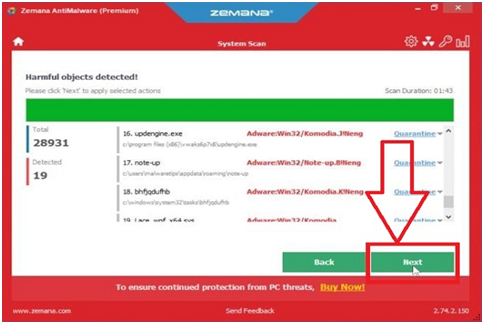
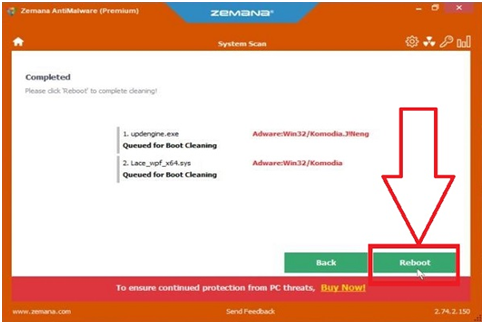
Step #33. Zemana AntiMalware may need to restart your computer once the malware removal method is finished. To reset your PC, click the “Reboot” button.
Final Words:
With the help of information related to csrss exe trojan, now you can understand the actual meaning of what Is Csrss Exe TorJan And how does it work. If you think that this article provided you the useful information, then shares your experience with us in comments. If you want to know anything related to topic or windows, then ask us in the comment.



Reply